This post is brought to you by 3M Company. The content and opinions expressed below are that of The Nerdy Nurse.
As a healthcare professional I am keenly aware of how important it is to keep protected health information (PHI) away from prying eyes. The Health Information Portability and Accountability Act (HIPAA) dictates strict laws and fines associated with breaches of this protected data. In addition, as a nurse I care for patients that are in their most vulnerable state. It is my responsibility to make sure they are protected and provided this best possible care. This means ensuring that in addition to administering medications and procedures on time, I will also protect their personal privacy and health data.
Before we go too much further we must first define visual privacy and visual hacking:
- Visual privacy is the issue of sensitive information being accessed visually via screens creating a security risk for organizations . Learn More About Visual Hacking
- Visual hacking is the active threat of sensitive, confidential or private information being viewed or captured for unauthorized use
Visual Hacking is a Legitimate Threat
One of the easiest ways that healthcare information can be stolen is simply by looking over a nurse’s shoulder and seeing the health data on the screen. Many healthcare organizations leave their patient data at risk by not using privacy filters on laptops, mobile devices, or even computers at the nurse’s station. I remember visiting an ER to learn more about the EHR system in use and being mortified by the fact that not only were their screens lacking privacy filters, but one of the computers was facing the hallway area and 100% visible to patients, unlicensed staff, security, and family members. I was so upset that by this, but when I brought up the security issues this presented the staff were quick to defend this practice stating it was the only way they could get certain physicians to document in the EHR.
Nurses that work in home care also have unique scenarios that present opportunities for data breaches. Their work outside of a traditional healthcare setting increases the risk for data breaches. In fact, in a recent Visual Data Breach Risk Assessment Study, Thomson, Herbert H, PhD. reported that “Two-thirds of working professionals display sensitive information on mobile devices outside the office.” Another study conducted by the Ponemon Institute/Experian Data Breach Resolution Report reports that visual privacy is violated or hacked “69% in the workplace, 55% while traveling, and 51% while in a public places such as a cafe or hotel.”
In healthcare, data security is everyone’s job. Your system is only as good as your weakest link. If you have the most powerful antivirus and firewall solutions it won’t matter if you have a single computer screen that is 100% visible to patients and their visitors.
In order to protect against visual privacy hacking, a few key standards must be in place:
Privacy Filters
The first step to maintain visual privacy and avoid visual hacking is to install privacy filters on any laptop or monitor that is not in a protected area. This means that any computer at a nurse’s station, registration area, or similar should have a privacy filter in place. Secured locations like IT departments or billing offices do not have visitors frequently and likely won’t require the filters.
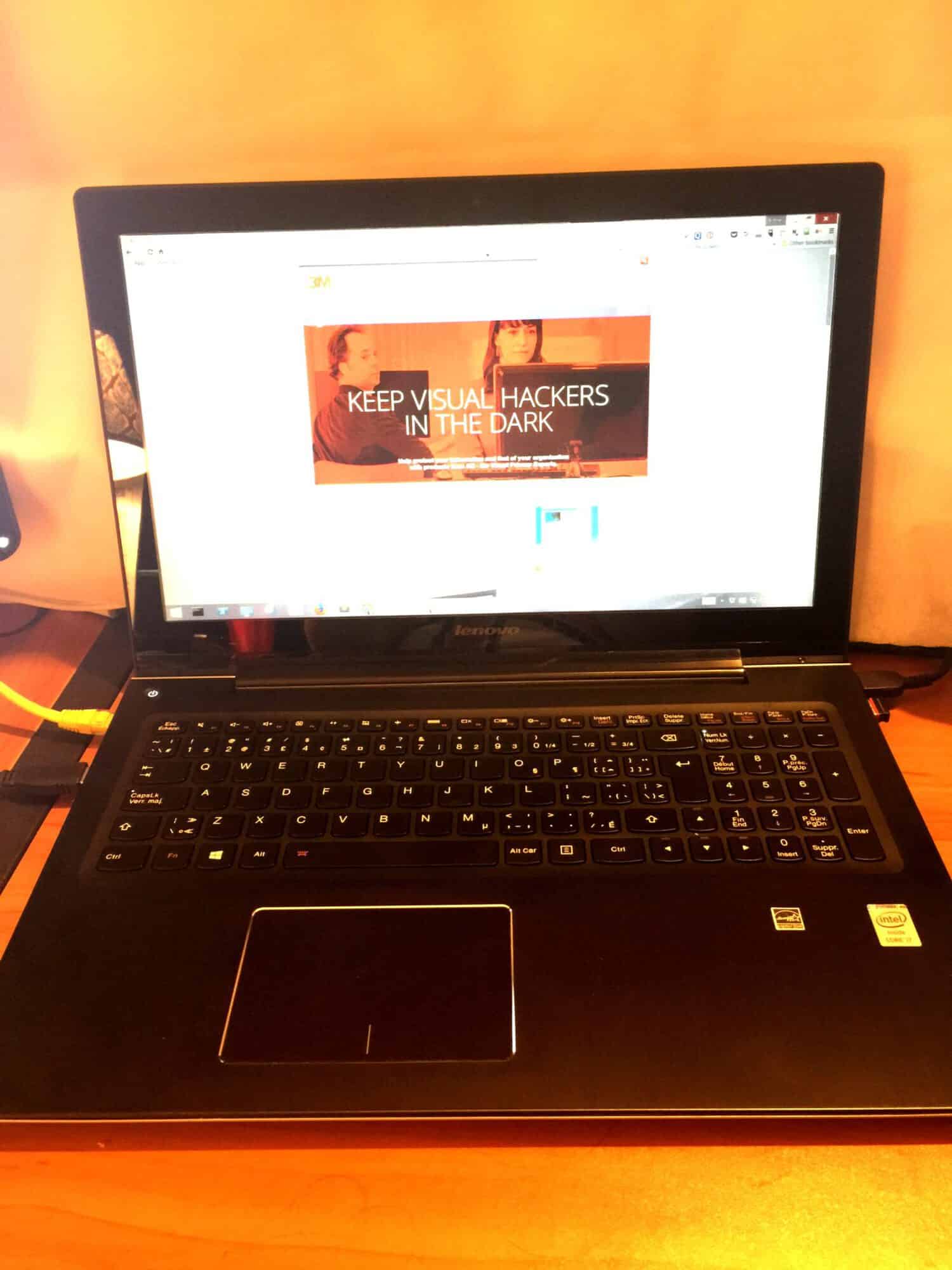
3M is a leader in visual privacy solutions and I have had the ability to personally test their products. They create privacy filters for pretty much any device you need including smartphones, tablets, laptops, and desktop screens. In fact, 3M was a pioneer of the original black-out privacy filters and their technology has advanced significantly since then. 3M visual privacy products allow users to see their screen clearly while prying eyes to the side of them see only a black screen.
Learn More About 3M™ Privacy Products
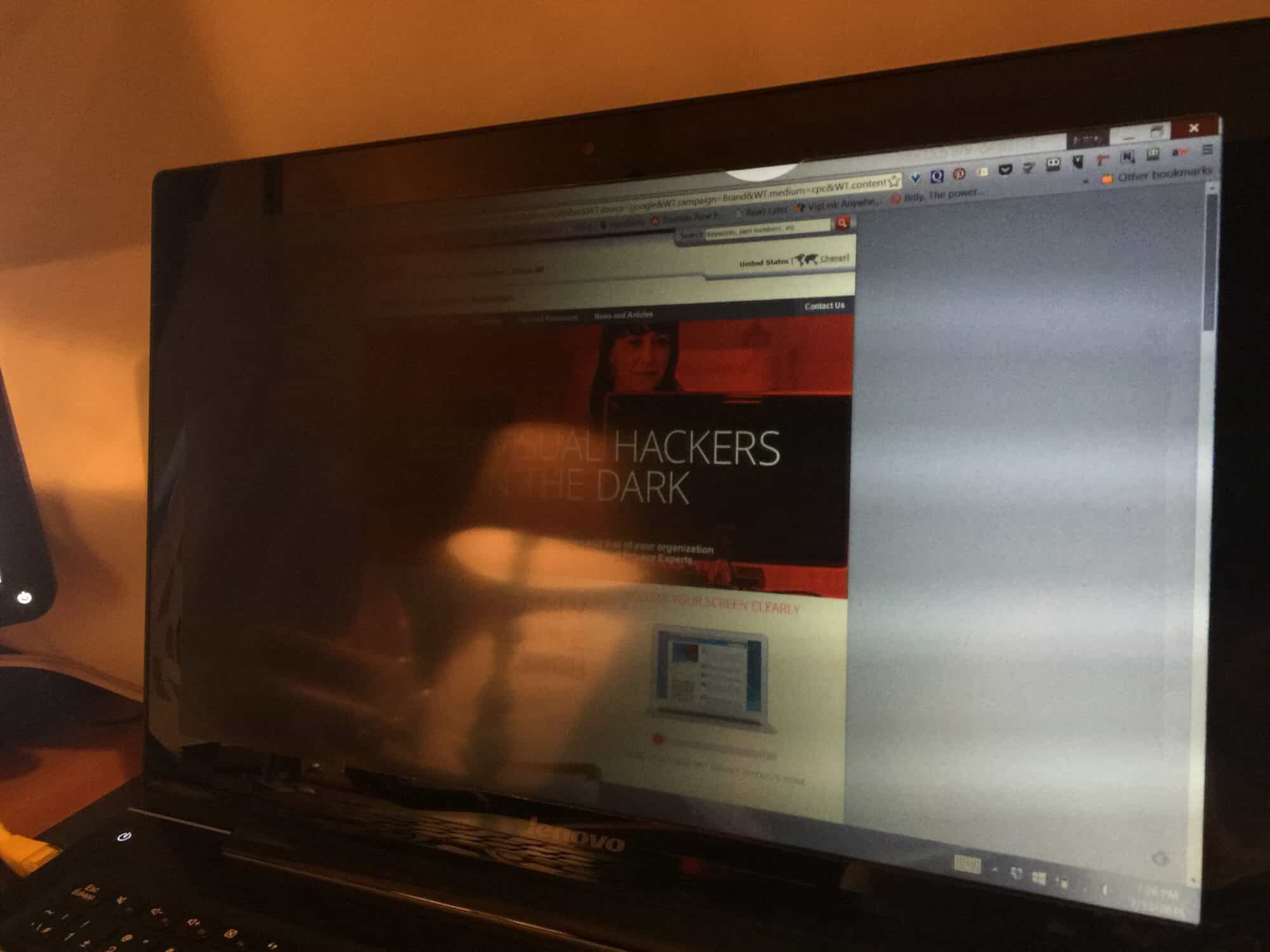
Securing Work Environments and PCs When Not in Use
Another risk for data security in the healthcare environment is not ensuring secure areas stay secure. IT departments, for example, should carefully monitor the staff they allow to be present in their secured locations. Contractors and other persons who are not direct employees of the hospital should not be left alone in environments where protected data could easily be visible on a computer. In addition, auto locks and screensavers should be put in place to make sure that if an employee leaves an area without securing their computer that it will automatically be secured after a designated amount of time.

Ensure Your Leadership Team is Onboard with Visual Privacy Security
Every year healthcare organizations lose millions of dollars in potential revenue due to bad press and other issues related to data breaches. The 2014 Cost of a Data Breach Study: Global Analysis showed that the average organization loses $5.8 million per data breach. Healthcare leaders are aware of these threats to their bottom line. They likely already have software tools in place to protect the EHR, but may be overlooking physical mechanisms to protect data. 3M privacy solutions can help corporate leaders be responsible in providing tools to workers allowing them to protect information from being visually hacked while maintaining productivity. Request a Sample of a 3M privacy and screen protectors today.
Risk of Visual Hacking
Consider the healthcare facility you work for or have visited and ask yourself this question:
Are there opportunities for visual hacking at healthcare organizations you have worked at or visited?
Download Nurse Bingo Today!
Liven up any shift with a fun game of bingo. See who can fill a row first!
Fill a whole card and lose grip with reality.
Your privacy is protected. We will never spam you.